Using the Wireshark Plugin to Analyze Packets Between vRouter and vRouter Agent on pkt0 Interface¶
- data:
2020-12-04
Wireshark is a an application that analyzes packets from a network and displays the packet information in detail.
OpenSDN Release 2008 and later supports the Wireshark
agent_header.lua plugin, which enables you to capture and analyze
the packets exchanged between a vRouter data plane and vRouter agent.
You can capture the packets by executing the vifdump -i 2 and the
tcpdump -i pkt0 commands in DPDK mode and kernel mode respectively. In
release 2008, the Wireshark agent_header.lua plugin is supported on
Macintosh OS computers only. .Starting from release 2011, the Wireshark
agent_header.lua plugin is supported on Macintosh OS as well as
Windows OS computers. Wireshark also enables you to add agent header
information to the captured packets.
Before you begin
You must ensure that the Wireshark application is installed on your computer. You can download Wireshark from the Download Wireshark page.
Configuration
Follow these steps to configure the Wireshark plugin and dissect agent header information in a packet:
Download the Wireshark plugin from GitHub: https://github.com/opensdn-io/tf-vrouter/tree/master/utils/agent_hdr_plugin.
Copy the plugin in to the following Wireshark directory on your Macintosh OS computer:
/Applications/Wireshark.app/Contents/PlugIns/wireshark/.Verify that the
agent_hdr.luaplugin is loaded successfully in Wireshark. Relaunch Wireshark and navigate to to verify that the plugin is loaded in the Plugins section.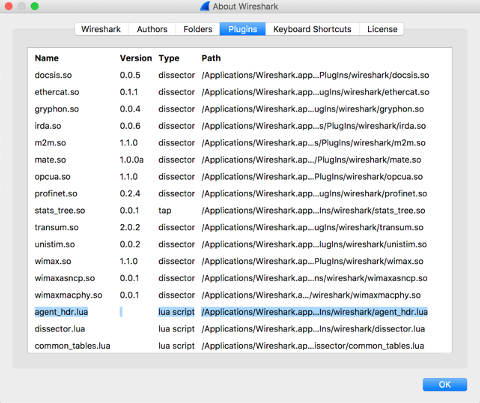
Pass the pcap file through editcap to add a custom encapsulation type for a packet:
editcap -T user0 <pcap-file-to-be-read> <output.pcap>In Wireshark, navigate to .
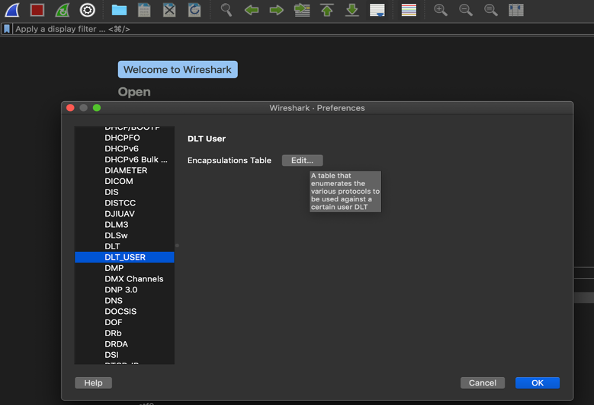
In the Edit Encapsulation Table, add the
agent_hdras a payload protocol for the packet.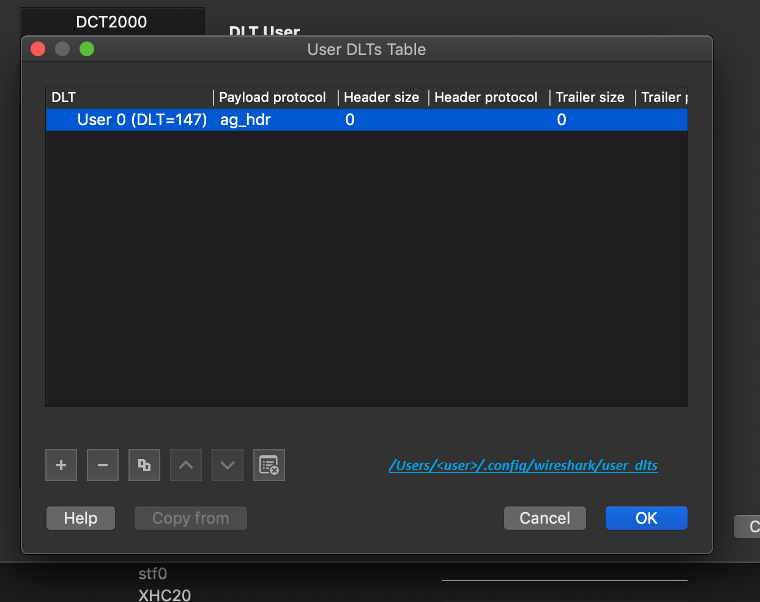
Using Wireshark, open the modified pcap file you generated in step 4. Wireshark displays the parsed packets.
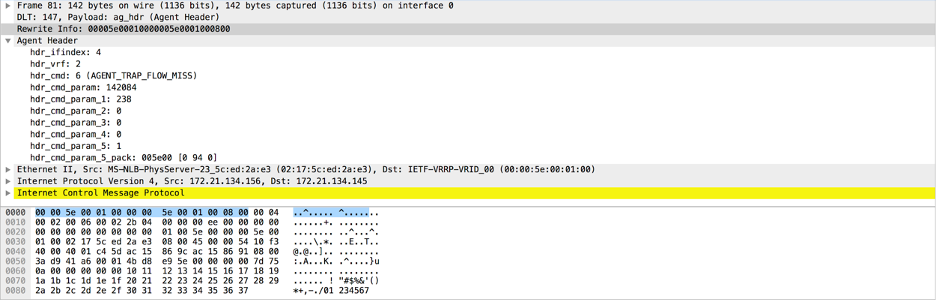
Follow these steps to configure the Wireshark plugin in a Windows OS computer and dissect agent header information in a packet:
Download the Wireshark plugin from GitHub: https://github.com/opensdn-io/tf-vrouter/tree/master/utils/agent_hdr_plugin.
If you are using Windows 32-bit OS, copy the plugin in to the following Wireshark directory on your computer:
C:\Program Files (x86)\Wireshark\.If you are using Windows 64-bit OS, copy the plugin in to the following Wireshark directory on your computer:
C:\Program Files\Wireshark\plugins\.Verify that the
agent_hdr.luaplugin is loaded successfully in Wireshark. Relaunch Wireshark and navigate to to verify that the plugin is loaded in the Plugins section.Open command prompt in Run as administrator mode and navigate to
C:\Program Files\Wiresharkto use editcap. Pass the pcap file through editcap to add a custom encapsulation type for a packet:editcap -T user0 <pcap-file-to-be-read> <output.pcap>In Wireshark, navigate to .
In the Edit Encapsulation Table, add the
agent_hdras a payload protocol for the packet. See .Using Wireshark, open the modified pcap file you generated in step 4. Wireshark displays the parsed packets.
The agent_header.lua plugin is also available in contrail-tools
container. You must perform the following steps to use the plugin from
the contrail-tools container:
Log in to vRouter as a root user.
Use the following command to view the summary of eachpacket in the pcap file:
tshark3_2 -nr <pcap file> -o “uat:user_dlts:"User 0(DLT=147)","ag_hdr","0","","0",""” -t ad
Use the following command to view detailed informationof the packets in the pcap file:
tshark3_2 -nr <pcap file> -o “uat:user_dlts:"User0 (DLT=147)","ag_hdr","0","","0",""” -T pdml
Release |
Description |
|---|---|
2011 |
Starting from release 2011, the Wireshark |
2011 |
OpenSDN Release 2008 and later supports the Wireshark
|